-
Posts
103,842 -
Joined
-
Last visited
-
Days Won
5
Content Type
Profiles
Articles
Services
Forums
Events
Downloads
Blogs
Store
Gallery
Everything posted by Administrator
-
Effective moderation features are essential for online communities. Forums, blog entries and member-to-member messaging are particularly attractive for spam bots and nuisance users alike. IPS Social Suite has always been best in class when it comes to moderation features with features like the free IPS Spam Service that are completely unmatched by other web applications. Over this series of 5 blog entries I'm going to introduce you to some of the new moderation features in the IPS Community Suite 4.0. Part 1: Setting up moderators Part 2: Approval Queue (New Feature) Part 3: Reports Part 4: Effective Moderation Part 5: Warnings Up until now, each application has been responsible for managing it's own moderator permissions (for example, you go and set up a moderator in the forums app, then in the gallery app, etc.) and there's been a concept of "global" or "super" moderators who can perform all moderator actions in all applications. In IPS Community Suite 4.0, we're centralising the creation and assigning of moderator permissions, and are doing this separate from groups (so you can now make just a member a moderator without putting them in a special "moderator" group). It works very similar to Admin Restrictions in 3.x. Here is the Moderators page: (In this screenshot I've given moderator controls to everyone in the groups Administrators or Moderators, and to the user "Brandon") When editing a moderator you see all of the permissions available across all applications. This screenshot shows global moderator permissions which apply across all applications: If you do not want to allow any of these globally, you can make them available only to certain areas - when any option is toggled off, the equivalent option will show under each application tab, along with an option to select which areas of that application it can be done in. For example, if I disable the "Can edit all content?" option, a "Downloads" tab appears with the following options: This allows me to choose what the moderator can edit, and in which categories they can do it. A similar tab appears for each application I have installed, or additional options appear on the tabs. Also when editing a moderator I can control permissions not related to content, for example, how they can use the warning system: Member management permissions: And more. When editing a moderator, I also have the option to "Give All Permissions" which makes them akin to "global" or "super" moderators in 3.x. When editing a member which has been given all permissions, I will see a message reminding me that if I remove any permissions they will no longer be a global moderator: Attached Thumbnails View the full article View the full article
-

Windows - Copy domain profile to local profile
Administrator replied to Administrator's topic in Programming Tip's & Trick's
Alternate method- create a new local admin user and then log in to it. Open regedit and browse to HKLM\Software\Microsoft\WindowsNT\CurrentVersion\ProfileList Under the SID for the new user, change the profile path to the location of your current profile. Then run unjoin (download it) and reboot. When you log in to the new local user, all the settings under the old domain profile will be used. -
How to convert your Domain Profile to a Local Profile This is useful when you have been doing consultant work on your own laptop, while joined to a clients domain, and you wish to leave said company while still retaining all the work and setting you had while joined to their domain. I’ve found doing a manual transfer to be more reliable then using the inbuilt profile copy (the one where you go into profiles and right click copy) and personally i haven found USMT (user state migration tool) to miss stuff or just totally screw up the new profile. To manually copy the profile over here are the steps. 1. know the name of the folder of the original domain profile. 2. log onto your computer locally as your new account (you don’t have to leave the domain to do this) 3. know the name of the folder for your new local account. 4. reboot the computer (important as files could be left open from either account and not be able to be copied or copied over) 5. log on as a different user from the above with local admin rights. 6. go into the domain folder profile (it would be under C:\Documents and Settings\domainusername) 7. highlight the contents of this folder and and copy all (make sure everything is unhidden) 8. go into the folder of the new local account and paste everything on top (Note, this will destroy everything in the current local account, so best to use a new local account to do this) (the reason why we paste the contents of the folder and not the folder itself or just rename the folder is because the local folder you are in now as a special SID associated with the local account) 9. since your logged in as the local admin now, make sure you check to make sure your new local account is a local admin as well 10. reboot the computer and log in as the local user, make sure everything looks correct, the best way to make sure everything worked is make sure your desktop background is correct, go into my documents and make sure you can see all the documents you had in there, if you cannot, then it sounds like a rights issue which is easily fixed. 11. If everything is not working now, it’s a rights issue, open up windows explorer, go to your folder (the one under documents and settings) right click on your folder, go to the permissions, take ownership of the entire folder and child contents, then add your admin rights to the folder and all child contents. Reboot again and you should have your entire domain profile copied over to your local profile, the thing i like about this method is it also leaves your original domain profile intact just in case of any issues (as long as you have the hard disk space.
-
For many years, IP.Board has featured a "Moderating Team" page where the community moderators are listed so that users can quickly and easily identify who to contact in the event they need assistance. This page has typically been a somewhat generic table-style view of users who are a moderator of some level. The page is not configurable and has limited usefulness and relevance when you consider the entirety of the suite. It is a relic of an older age and it really stood out as needing an overhaul, so that is exactly what we have done in 4.0. Configurable As mentioned above, the moderating team page has never been configurable in IP.Board. If a user is a moderator (either a super moderator, or a forum-level moderator) then they are displayed on this page. The users are displayed in basic alphabetical order in a table-style view and you cannot easily see which user is responsible for which roles on the site. Furthermore, if you add a moderator to another application (for instance, IP.Downloads or IP.Gallery) then they may not be displayed on this page if they aren't also a moderator in the forums. We have completely done away with the way this page used to work and rethought it from the ground up. Its purpose is simple: show the viewing user which users on the site are "important" and their relevance to the site. To implement our goal, we have decided to make the entire page configurable. In the admin area you can now create groupings for this page. This means that you can put some users in one group, some users in another group, and so on in order to better reflect the hierarchy of your organization. For instance, here at IPS we would list Management staff at the top, followed by Developers, followed by Support Agents, and possibly followed by community moderators. You can reorder the groups however you see fit to ensure that the most important users are listed first. You can also now associate a template with each group. When you view the staff page, you will probably want to show a little more information for the most important users, but you may want to just show simple links to a profile for the regular community moderators. By default we will ship with 3 or 4 basic templates that we feel will allow you to display staff groups in different ways to better reflect your organization, however any administrator can add new templates by simply creating a template with the appropriate prefix in the appropriate template group. When you add users to a group, you can specify a custom name to show (which will fall back to the member's username), you can specify a custom title to show (which will fall back to the member's title) and you can specify a bio to show. Users who are displayed on this page can edit their details right from the staff page directly. Viewing the page We wanted to allow this page to be set up to better reflect the staff on a community. A simple listing of moderators is no longer relevant for many users of the Community Suite - you may want one moderator to not be displayed because they only manage pre-sales questions, or you may want an administrator who is not a moderator to be displayed, or perhaps you want to create a game roster instead of displaying staff but you don't want to give those users moderator privileges on the site. Now you can do that, and you can better present the page to your users. As you can see here, the first grouping (labeled "Management") is displayed in full width. The second grouping called "Developers" are blocks that take up half of the available width. The last grouping called "Support Agents" are rows of 4 blocks each. It is important to note that the interface is subject to change and we are still putting some finishing touches on this screen, however hopefully the screenshot will give you a good idea of how the page can be laid out to improve communication between your staff and your visitors. Attached Thumbnails View the full article View the full article
-
Almost all of our applications support commenting or reviewing to some degree. You can comment on events in IP.Calendar, images in IP.Gallery and blog entries in IP.Blog, and you can review products in IP.Nexus, for instance. The differences between reviewing and commenting are subtle, yet important. Commenting allows you to say something about a content item that has been contributed, while reviewing is intended to allow you to give feedback about the item based on your experience. You should not be able to review something you have not seen or used, for instance, and you should only be able to review it once. We have worked on developing these concepts further for 4.0, and bringing both capabilities easily to all applications in the suite. Comments Any application in the 4.0 suite can support commenting easily. From a development perspective, you need only create a content comment class that extends IPSContentComment (and define a few methods in this class, such as how to generate the URL to the comment), and then in your main content item class you specify this new content comment class in a specific property. For example, with IP.Downloads we have the following in the content item class /** * @brief Comment Class */ public static $commentClass = 'IPSdownloadsFileComment';And then there is, as you would expect, a commenting class found at IPSdownloadsFileComment which extends IPSContentComment. This comment class defines a few properties, and then defines a single url() method (which must return the URL to the comment). Almost everything else is handled automatically by the suite.Otherwise, comments work largely similar to the way they work in 3.x. Moderators can edit, hide, approve and delete comments. You can allow certain users to reply to locked content (e.g. to leave a comment on something that is locked), but otherwise locked content cannot be commented on. You can use multi-moderation on comments and you can quote and multi-quote comments. All of the functionality you would expect to see is still present. Reviews There are only a few primary differences between reviews and comments. You may only leave a single review on a content item. Once you have left a review, you will not be able to leave another. When leaving a review, you are presented with a 5-star panel from which you should select your star rating. Some applications may further restrict your ability to leave a review. For instance, there is an option in IP.Downloads to only allow users who have downloaded a file to leave a review. As of the 4.0 Community Suite, any application can now support reviews just as easy as commenting. Further, as a developer you can support both simultaneously (and, typically, the administrator can disable one or both systems if they choose). Reviews work almost the same as comments from an implementation perspective. You create a review content comment class, and you define a specific property in the content item class. For IP.Downloads you will see this in the content item class /** * @brief Review Class */ public static $reviewClass = 'IPSdownloadsFileReview';And then you will find a review class at IPSdownloadsFileReview, which extends IPSContentReview (which in turn actually extends IPSContentComment). The review class for IP.Downloads, just like the commenting class, only contains a single method to define how to generate the URL, as well as a few required properties.When reviews are left and a star rating is applied, this rating is averaged and applied to the content item. A content item could in theory support both the traditional star rating system (like you might see in IP.Downloads or even in IP.Board in the 3.x product line) and reviews at a technical level, however it is recommended to prevent confusion that you either use the traditional rating system OR reviews, but not both simultaneously. Most applications in 4.0 that support reviews will not support the traditional rating system as a result. You will note in this screenshot that because I have not yet downloaded the file (which is an optional reviews-related restriction in IP.Downloads) that I am unable to review the file at present. When a user does not have permission to do something, the 4.0 community suite makes every effort to clearly indicate why the user is unable to accomplish a given task. Other users reading a review can determine if they found the review helpful or not (although you are unable to specify this on your own reviews of course), and these yes/no votes are subsequently tallied in order to allow users to sort reviews by "most helpful" per the sorting buttons at the top right of the above screenshot. Wrapping up Applications are capable of displaying either reviews or comments (or both) in any manner they wish, however you will find that most applications in the 4.0 suite that support reviews and/or comments will display them in a fashion similar to the above screenshots (noting all the typical "these are early screenshots and the final product may appear different" disclaimers). By supporting both of these similar yet slightly different functionalities out of the box, we believe our first party applications as well as third party applications by our talented development community can really shine and allow end users to interact with the community in logical and focused ways. We hope these changes allow you to set up your own community to cater to your users in the manner best suited to your community. Attached Thumbnails View the full article View the full article
-
IP.Calendar has supported basic recurring calendar events for many versions now. You can create events that recur weekly, monthly or yearly in IP.Calendar, and they will automatically show up on their specified schedule. While this capability is certainly useful, we felt it was time to enhance event recurrence capabilities in the next version of IP.Calendar. New options Recurring every week, month or year is useful, but there are many other ways events can recur and IP.Calendar has no provisions to accommodate those recurrence types in the 3.x IP.Calendar release. For 4.0 we have added several new recurrence-based options to the calendar. Recur daily, weekly, monthly or yearly In addition to the three options available in previous versions, you can now configure events to recur daily. Recurrence frequency You are no longer restricted to recurring every week (or month or other time period). You can now configure events to recur every 2 weeks, or every 3 months, or every 10 days, or whatever period of time you need to. Weekly recurrence: days of the week If your event recurs weekly, you can now specify the days of the week the event should recur on. This means you can configure an event that recurs weekly on every Tuesday and Thursday, for instance. Recurrence timeframe In previous versions of IP.Calendar, the end date specified when the event should stop recurring. In 4.0, the end date/time specifies when the original recurrence end date/time are. This means you can have an event that lasts 2 days and recurs annually, for instance (in other words, recurring ranged events). When configuring the event, you now have three options for specifying the recurrence information: Never end End after a certain number of occurrences End on a certain date You can now configure events like Christmas which never end, you can configure meetings which have a certain number of occurrences before they are finished, and you can configure recurring events that end on a certain date. As you can see, the options have been greatly expanded to accommodate many more types of recurring events. Some technical details At a technical level, event recurrence data is stored as an "RRULE", just like the iCalendar specification will specify. In fact, the data should be a 1:1 equivalent. If you import iCalendar events which have recurrence capabilities not supported by calendar, those events will be skipped during the import routine (as they are presently), however there are now far fewer recurrence capabilities that are wholly unsupported. By storing the exact RRULE value we have a few benefits over previous versions of Calendar: Event importing is simpler, as we can copy the rule directly into the database unmodified (after verifying we support all parameters) Event exporting is simpler for the same reason We can expand recurring event support in the future if necessary with few database changes necessary Using PHP you can easily find future event recurrence details using the nextOccurrence() method. /** * Find the next occurrence of an event starting from a specified start point * * @param IPScalendarDate $date Date to start from * @param string $type Type of date to check against (startDate or endDate) * @return IPScalendarDate|NULL */ public function nextOccurrence( $date, $type='startDate' )This instance method is run against a calendar event, passing in a date to find the next occurrence from. You can look for either start date or end date. Attached Thumbnails View the full article View the full article
-
The submissions process in IP.Downloads has a certain complexity that may not be apparent at first. As well as simple file uploads, we also support adding files from URLs and from the local file system, and screenshots can also be added in these ways. Which category you choose to submit to affects which of these options are available. In addition, via the AdminCP you can bulk-upload files - but not via the front-end. For IP.Downloads 4, we wanted to improve this process with interface and functionality changes. Submitting Files Here's a video demonstration of how creating a single file record in IP.Downloads works in v4: We've worked hard to improve the flow for users here - while they are uploading files (which may be large and take some time), they can continue adding the other file information such as screenshots and meta data. While that's happening, the upload progress is always shown at the top of the screen. In the video you'll also see how image uploading is handled, as well as prefixes in the tag system, which are now supported throughout the IPS Community Suite. Bulk Uploading Instead of going to the AdminCP to bulk-submit files, single- and bulk-uploads are now handled through exactly the same process on the front end. This means users can be granted bulk-upload permissions without requiring AdminCP access, a big improvement on the current implementation. To bulk upload, a user clicks the "Submit a file" button as normal, and chooses "I want to submit multiple files at once". They see the same upload area, but this time, the file information step is handled separately after the page is submitted. Each uploaded file has a separate block for file information and its own set of screenshots. We'll of course be showing more of the IP.Downloads homepage and file view later, but we hope that gives you a taste of what to expect in IP.Downloads in IPS4. Attached Thumbnails View the full article View the full article
-
Following content is an important aspect of interacting with your community. It allows you to be notified when there are updates to the content or when other users comment on the content, and it allows you to find content you are interested in at a later date. We have taken the opportunity with 4.0 to enhance the system where-by users can follow content in the IPS Community Suite to simplify and clarify certain processes, make it easier to follow content you submit, and to be sure you are receiving the notifications you wish to receive. Following your own content One area of improvement that was identified during planning meetings for 4.0 was the process of following your own content. While the forums have a method in place already to follow new topics you create (or to automatically follow topics you reply to), the rest of the suite has no such similar capability in place. We wanted to make it easier for users to follow the content they are submitting to make it more likely they will be aware of comments posted to their submissions, in turn making it more likely they will return and continue to interact with the community. In all applications in 4.0, when submitting new content you will have the ability to follow that content right away. When replying, similarly there is an option to automatically follow the content you are replying to. In your Notification preferences panel, you can choose to automatically follow new content submissions by default and you can choose to automatically follow content you reply to by default (in which case the appropriate checkboxes would be checked by default during submissions and commenting). These options affect your content submissions and comments across the entire suite in 4.0. Following other content You can follow other content submitted to the community by clicking on the "Follow" button available in the appropriate area. As with 3.x, you can follow containers (e.g. follow a forum or an IP.Downloads category), and you can follow content items (e.g. a topic or an IP.Downloads file). You can follow content items and containers both publicly, which means others will be able to tell you are following that item, and anonymously, where you will receive notifications of updates to the item but others will not be able to see you are following it. You can choose to receive an email notification immediately when there is a reply to the content, or you can choose to receive a daily or weekly digest. Digest notifications have been expanded suite-wide and are now supported in all applications automatically. As with 3.x, you can choose to receive an email notification or an inline notification on the site (or you can choose to receive neither or both if you prefer). One common issue encountered in IP.Board 3.x was that users would follow something, however their notification preferences were configured in a manner which meant they would never subsequently be notified of updates to the item they are following (because they have chosen not to receive neither email nor inline notifications for that follow method). The 4.0 suite recognizes this scenario and warns the user in this event. Summary We have worked to improve and clarify the follow system where possible in the 4.0 suite, while still retaining the same level of functionality and flexibility you have available in 3.x. The ability to automatically follow new submissions should help users remain engaged on your site when other users comment on their contributions, bringing them back and enticing them to continue contributing to your site. The improved clarification when users will not receive notifications due to their preference configuration will help reduce staff overhead in answering questions, as well as visitor confusion and frustration. We will talk about notifications themselves in a future blog entry, however we hope these changes help improve usability and interaction with your site by your visitors. Attached Thumbnails View the full article View the full article
-
cPanel TSR 2014-0002 Full Disclosure Case 89985 Summary Disclosure of cpanel-horde’s MySQL password due to world-readable backups. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description During the upgrade to Horde 5 on 11.42 systems, a backup tarball of the existing Horde configuration files is created. This backup tarball was created in a world-accessible directory with world-readable permissions, allowing local accounts to see the MySQL password for the shared cpanel-horde user. Credits This issue was discovered by Rack911. Solution This issue is resolved in the following builds: 11.42.0.6 For the PGP-signed message, see http://cpanel.net/wp-content/uploads/2014/02/TSR-2014-0002-Full-Disclosure.txt. View the full article
-
cPanel TSR-2014-0002 Announcement cPanel has released a new build for the 11.42, CURRENT, and EDGE update tiers. This update provides targeted changes to address security concerns with the 11.42 release of the cPanel & WHM product. This build is currently available to all customers via the standard update system. cPanel has rated this update as having a security impact level of Important. Information on cPanel’s security ratings is available at go.cpanel.net/securitylevels. If your deployed cPanel & WHM servers are configured to automatically update when new releases are available, then no action is required. Your systems will update automatically. If you have disabled automatic updates, then we strongly encourage you to update your cPanel & WHM installations at your earliest convenience. RELEASES The following cPanel & WHM versions address all known vulnerabilities: * 11.42.0.6 & Greater The latest public releases of cPanel & WHM for all update tiers are available at httpupdate.cpanel.net. SECURITY ISSUE INFORMATION Independent security researchers identified the security issue resolved in this update. There is no reason to believe that this vulnerability is known to the public. As such, cPanel will only release limited information about the vulnerability at this time. Once sufficient time has passed, allowing cPanel & WHM systems to automatically update to the new version, cPanel will release additional information about the nature of this security issue. Additional information is scheduled for release on February 14th, 2014. For information on cPanel & WHM Versions and the Release Process, read our documentation at go.cpanel.net/versionformat. For the PGP signed message, please go to TSR-2014-0002 Announcement View the full article
-
2/10/2014 Houston, TX - cPanel, Inc. has released EasyApache 3.24. This version removes Apache 1.3/2.0, PHP 5.2, and mod_frontpage. As mentioned in Introducing EasyApache’s Optimal Profiles, these End of Life (EOL) items are no longer available in EasyApache. These items have been removed for the following reasons: They are no longer supported by their respective developers. They include unpatched CVEs (Common Vulnerabilities and Exposures). EasyApache provides the most up-to-date, supported versions of Apache (2.2/2.4) and PHP (5.4/5.5). Keep in mind that viable alternatives to mod_frontpage exist, such as WebDAV and FTP. Also, PHP 5.2 and mod_frontpage are available as custom modules (“opt mods”). Important: Starting May 11, 2014, EasyApache users running EOL cPanel & WHM versions (11.38 and older) will no longer receive EasyApache updates. These users will still be able to rebuild EasyApache using the latest release prior to May 11, 2014. A message will appear in the WHM user interface and command line interface warning EasyApache users of this change. EasyApache users running cPanel & WHM version 11.38 will not see this message until that version reaches EOL at the end of April 2014. To learn how to upgrade your version of cPanel & WHM, visit http://go.cpanel.net/upgradeversion. To ensure that you receive up-to-date product news from cPanel, we encourage you to subscribe to the “Security Advisories and Product Release Announcements” mailing list here: http://cpanel.net/mailing-lists View the full article
-
Place the following in your .htaccess file inside the directory as needed. 2592000 = 30 days etc, change as needed <FilesMatch "\.(gif|png|jpg)$">Header set Cache-Control "max-age=2592000, public"</FilesMatch>
-
Case 84385 Summary Arbitrary code execution as cpanel-horde user via cache file poisioning. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description The Horde Webmail interfaces accessible to cPanel and Webmail accounts uses PHP serialized cache files to speed up some backend operations. By default these cache files were stored in the world-writable /tmp directory with predictable names. A malicious local attacker could pre-create the cache files inside /tmp, potentially leading to arbitrary code execution as the cpanel-horde user. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 86341 Summary Arbitrary file read as root during cPanel account creation for ACL limited resellers. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description An ACL limited reseller could send crafted inputs to WHM’s account creation functionality to combine multiple path traversal attacks in the package extensions subsystem. This flaw would store the contents of the destination file into the new account’s cpuser file. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 Case 86381 Summary Disclosure of root’s accesshash to ACL limited resellers via WHM xml-api. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description Reseller accounts, regardless of their ACLs, were able to retrieve and alter root’s accesshash credentials via the get_remote_access_hash XML-API command by supplying empty user and password arguments. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 86453 Summary Injection of arbitrary settings into cpuser files via account creation. Security Rating cPanel has assigned a Security Level of Moderate to this vulnerability. Description The WHM /scripts5/wwwacctform interface allowed the injection of newlines into the ‘locale’ and ‘cpmod’ parameters. These injections could be used to set values in the newly created account’s cpuser file that were not permissible with a reseller’s ACL restrictions. Credits This issue was discovered by Rack911. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 86461 Summary Overwriting of trusted inputs to third party hooks scripts. Security Rating cPanel has assigned a Security Level of Moderate to this vulnerability. Description An ACL limited reseller could provide additional form inputs to WHM’s create and modify account interfaces containing null bytes in the parameter name. When these inputs were passed on to third party hook scripts though an exec() call, the additional parameters would be truncated to match parameter names that are normally anchored in trust for the third party hook scripts. Third party hook scripts are provided the raw inputs to the functions they extend and are responsible for validating these inputs. Since null bytes do not transfer through the hook script interface correctly, any form parameter names submitted with null bytes will now result in an error. Credits This issue was discovered by Rack911. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 86857 Summary Limited arbitrary file overwrite for ACL limited resellers via domain parking. Security Rating cPanel has assigned a Security Level of Moderate to this vulnerability. Description The owner parameter to the WHM /scripts/park interface was not correctly validated. By injecting a path traversal attack into this parameter, reseller accounts with the ‘park-dns’ ACL could overwrite arbitrary files on the system with a Perl storable file with predictable contents. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 87317 Summary Arbitrary code execution as root for ACL limited resellers via cluster configuration interfaces. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description Resellers with the ‘clustering’ ACL could inject data using newlines and NUL bytes into the form parameters of the cluster configuration interfaces. This flaw could then be leveraged to execute arbitrary code as root via string eval()s in various other interfaces. Credits This issue was discovered by Rack911. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 87433 Summary Injection of arbitrary settings into cpuser files via mxcheck setting. Security Rating cPanel has assigned a Security Level of Moderate to this vulnerability. Description The WHM /script2/savemx and /cgi/zoneeditor.cgi interfaces allowed resellers with the “edit-mx” or “edit-dns” ACLs to modify the mxcheck setting for accounts under their control. By injecting newlines into this setting, a malicious reseller could alter other settings for the account that are stored in the account’s cpuser file. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 87437 Summary ACL limited resellers allowed to disable digest authentication for arbitrary accounts. Security Rating cPanel has assigned a Security Level of Minor to this vulnerability. Description Due to a lack of ACL enforcement, an ACL limited reseller could disable digest authentication for any account on the system using WHM’s XML-API. The ACL protections for this functionality have been updated to require that ACL limited resellers own any accounts they modify in this fashion. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 87625 Summary ACL limited resellers allowed to restore backups for the accounts they control. Security Rating cPanel has assigned a Security Level of Minor to this vulnerability. Description The WHM XML-API allowed all resellers to restore backups for any accounts they own. The equivalent functionality in WHM’s HTML interfaces restricted the ability to restore accounts from backups to resellers with the “all” ACL. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 88061 Summary Mis-assignment of IP addresses for ACL limited resellers via createacct. Security Rating cPanel has assigned a Security Level of Moderate to this vulnerability. Description With certain combinations of IP delegations and free IP address space, reseller accounts with the ‘add-pkg-ip’ ACL could install new accounts onto IP addresses delegated to another reseller. This might allow a malicious reseller account to capture web traffic intended for other accounts on the system. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Case 88341 Summary Arbitrary code execution for ACL limited resellers during account creation. Security Rating cPanel has assigned a Security Level of Important to this vulnerability. Description A flaw in the new account creation process resulted in the Ruby ‘gem’ command running with the effective UID of the newly created user and the real UID of root. A malicious reseller account could leverage this flaw to execute arbitrary Ruby code with root’s UID during the account creation process. Credits This issue was discovered by the cPanel Security Team. Solution This issue is resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 Multiple Cases (55) Summary Multiple XSS vulnerabilities in various interfaces. Description Output filtering errors in several different interfaces allowed JavaScript inputs to be returned to the browser without proper filtering. The affected interfaces are listed below. Case: 84633 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/htaccess/deluser.html, /frontend/x3/indexmanager/changepro.html, /frontend/x3/indexmanager/dohtaccess.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 84877 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /scripts3/initial_setup_wizard4 Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Mathew Case: 84881 Security Rating: Moderate XSS Type: Stored Interface: cPanel URLs: /frontend/x3/mail/def.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Mathew Case: 84885 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /x3/mail/filters/editfilter.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Matthew Case: 84893 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mail/conf.html, /frontend/x3/mail/saveconf.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Mathew Case: 84897 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/stats/detailsubbw.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Mathew Case: 84901 Security Rating: Moderate XSS Type: Stored Interface: cPanel URLs: /frontend/x3/cpanelpro/filelist-thumbs.html, /frontend/paper_lantern/cpanelpro/filelist-thumbs.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Christy Philip Mathew Case: 85029 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mail/csvimport.html, /frontend/x3/mail/csvimport-step2.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Shubham Mittal Case: 85133 Security Rating: Moderate XSS Type: Stored Interface: cPanel URLs: /frontend/x3/filemanager/editit.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Shubham Mittal Case: 85177 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/cgi/Clock/docode.html, /frontend/x3/cgi/Countdown/docode.htm, /frontend/x3/cgi/Counter/docode.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Paweł Hałdrzyński Case: 85229 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/psql/deldb.html, /frontend/x3/psql/deldb.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 85249 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/psql/addusertodb.html, /frontend/x3/psql/addusertodb.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 85273 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mime/addhotlink.html Affected Releases: 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 85457 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mail/editmsgs.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Ankit Mittal Case: 85461 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mail/showq.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Ankit Mittal Case: 85589 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /scripts2/dotweaksettings Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Ernesto Martin Case: 85977 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /scripts/addpkg2 Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Olivier Beg Case: 85985 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /scripts2/edit_sourceipcheck, /x3/security/security-questions.html, /paper_lantern/security/security-questions.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: Olivier Beg Case: 86329 Security Rating: Important XSS Type: Stored Interface: WHM URLs: /scripts/doeditmx Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 87081 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/mime/add_redirect.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: SimranJeet Singh Case: 87417 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/err/erredit.html, /frontend/x3/filemanager/editit.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: SimranJeet Singh Case: 87457 Security Rating: Minor XSS Type: Self Interface: WHM URLs: /cgi/cpaddons_feature.pl Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88093 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/backup/fullbackup.html, /frontend/x3/backup/wizard-fullbackup.html, /frontend/paper_lantern/backup/fullbackup.html, /frontend/paper_lantern/backup/wizard-fullbackup.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88097 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/backup/doupload.html, /frontend/paper_lantern/backup/doupload.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88129 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/backup/dosqlupload.html, /frontend/paper_lantern/backup/dosqlupload.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88133 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/backup/doafupload.html, /frontend/paper_lantern/backup/doafupload.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88137 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/backup/wizard-dofullbackup.html, /frontend/x3/backup/dofullbackup.html, /frontend/paper_lantern/backup/wizard-dofullbackup.html, /frontend/paper_lantern/backup/dofullbackup.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88141 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/denyip/add.html, /frontend/x3/denyip/add.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88145 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/denyip/del.html, /frontend/x3/denyip/del.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88149 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/denyip/index.html, /frontend/x3/denyip/index.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88153 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/cpanelpro/filelist-convert.html, /frontend/paper_lantern/cpanelpro/filelist-scale.html, /frontend/paper_lantern/cpanelpro/filelist-thumbs.html, /frontend/x3/cpanelpro/filelist-convert.html, /frontend/x3/cpanelpro/filelist-scale.html, /frontend/x3/cpanelpro/filelist-thumbs.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88157 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/files/savefile.html, /frontend/paper_lantern/files/savefile.html, /frontend/x3/files/savefile.html, /frontend/x3/files/savefile.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88165 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/x3/files/extractfile.html, /frontend/paper_lantern/files/extractfile.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88173 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/files/showfile.html, /frontend/x3/files/showfile.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88181 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/fp/addfp.html, /frontend/paper_lantern/fp/delfp.html, /frontend/x3/fp/addfp.html, /frontend/x3/fp/delfp.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88209 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/htaccess/leechprotect/dohtaccess.html, /frontend/paper_lantern/htaccess/leechprotect/doleech.html, /frontend/x3/htaccess/leechprotect/dohtaccess.html, /frontend/x3/htaccess/leechprotect/doleech.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88213 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/net/dnslook.html, /frontend/x3/net/dnslook.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88229 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/park/dodelparked.html, /frontend/x3/park/dodelparked.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88253 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/psql/deluserfromdb.html, /frontend/x3/psql/deluserfromdb.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88257 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/stats/analog.html, /frontend/x3/stats/analog.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88261 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/addon/saveredirect.html, /frontend/x3/addon/saveredirect.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88265 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/subdomain/doadddomain.html, /frontend/x3/subdomain/doadddomain.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88269 Security Rating: Moderate XSS Type: Stored Interface: cPanel URLs: /frontend/x3/addoncgi/cpaddons.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88277 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/sql/PhpMyAdmin.html, /frontend/paper_lantern/backup/index.html, /frontend/x3/sql/PhpMyAdmin.html, /frontend/x3/backup/index.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88281 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/queuesearch.html, /frontend/x3/mail/queuesearch.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88285 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/cpanelpro/changestatus.html, /frontend/x3/cpanelpro/changestatus.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88289 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/editmsg.html, /frontend/x3/mail/editmsg.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88293 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/cpanelpro/editmsgs.html, /frontend/x3/cpanelpro/editmsgs.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88297 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/cpanelpro/msgaction.html, /frontend/x3/cpanelpro/msgaction.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88301 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/resetmsg.html, /frontend/x3/mail/resetmsg.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88305 Security Rating: Moderate XSS Type: Stored Interface: cPanel URLs: /frontend/paper_lantern/mail/conf.html, /frontend/x3/mail/conf.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88309 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/showlog.html, /frontend/x3/mail/showlog.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88313 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/showmsg.html, /frontend/x3/mail/showmsg.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88321 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/cpanelpro/editlists.html, /frontend/x3/cpanelpro/editlists.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team Case: 88325 Security Rating: Minor XSS Type: Self Interface: cPanel URLs: /frontend/paper_lantern/mail/conf.html, /frontend/x3/mail/conf.html Affected Releases: 11.42.0, 11.40.1, 11.38.2 Reporter: cPanel Security Team cPanel includes a comprehensive protection mechanism against XSS and XSRF attacks called Security Tokens. Security Tokens protection is enabled by default in all installs of cPanel & WHM. When Security Tokens protection is enabled, an attacker intending to utilize any self-XSS vulnerabilities must convince the victim to navigate their browser to the appropriate cPanel or WHM interface and manually input the JavaScript payload. Credits These issues were discovered by the respective reporters listed above. Solution These issues are resolved in the following builds: 11.42.0.4 11.40.1.10 11.38.2.16 For the PGP-signed message, see TSR-2014-0001-Full-Disclosure. View the full article
-
cPanel has released new builds for all public update tiers. These updates provide targeted changes to address security concerns with the cPanel & WHM product. These builds are currently available to all customers via the standard update system. cPanel has rated these updates as having security impact levels ranging from Minor to Important. Information on cPanel’s security ratings is available at http://go.cpanel.net/securitylevels. If your deployed cPanel & WHM servers are configured to automatically update when new releases are available, then no action is required. Your systems will update automatically. If you have disabled automatic updates, then we strongly encourage you to update your cPanel & WHM installations at your earliest convenience. RELEASES The following cPanel & WHM versions address all known vulnerabilities: * 11.42.0.4 & Greater * 11.40.1.10 & Greater * 11.38.2.16 & Greater The latest public releases of cPanel & WHM for all update tiers are available at http://httpupdate.cpanel.net. SECURITY ISSUE INFORMATION The cPanel security team and independent security researchers identified the resolved security issues. There is no reason to believe that these vulnerabilities have been made known to the public. As such, cPanel will only release limited information about the vulnerabilities at this time. Once sufficient time has passed, allowing cPanel & WHM systems to automatically update to the new versions, cPanel will release additional information about the nature of the security issues. This Targeted Security Release addresses 67 vulnerabilities in cPanel & WHM software versions 11.42, 11.40, and 11.38. Additional information is scheduled for release on February 5th, 2014. For information on cPanel & WHM Versions and the Release Process, read our documentation at: http://go.cpanel.net/versionformat For the PGP-signed message, see TSR-2014-0001-Announcement View the full article
-
cPanel & WHM software version 11.36 has reached End of Life. In accordance with our EOL policy [http://docs.cpanel.net/twiki/bin/view/AllDocumentation/InstallationGuide/LongTermSupport],11.36 will continue functioning on servers. The last release of cPanel & WHM 11.36, being 11.36.2.13, will remain on our mirrors indefinitely. You may continue using this last release, but no further updates, such as security fixes and installations, will be provided for 11.36. Older releases of cPanel & WHM 11.36 will be removed from our mirrors. We strongly recommend that all customers migrate any existing installations of cPanel & WHM 11.36 to a newer version (either 11.38 or 11.40). If your server setup complicates the process of migrating to a newer version of cPanel & WHM (for example, an out-of-date operating system), then cPanel is here to help. Simply open a support ticket at https://tickets.cpanel.net/submit so that our knowledgeable support team can provide recommendations, migration assistance, and more. About cPanel, Inc. Since 1997, cPanel, Inc. has been a leading innovator and developer of control panel software for the web hosting industry. cPanel builds software that allows web host professionals to transform standalone servers into fully automated, point-and-click web hosting platforms. cPanel-licensed software allows server and website owners, along with resellers and developers, to optimize their technical resources and replace tedious shell-oriented tasks with dynamic, intuitive web-based interfaces. For more information, visit http://cpanel.net. For the PGP-signed message, see 11.36-EOL. View the full article
-
1/30/2014 Houston, TX - cPanel, Inc. tentatively plans to release EasyApache 3.24 in the very near future. This version will include the removal of Apache 1.3/2.0, PHP 5.2, and mod_frontpage. As mentioned in Introducing EasyApache’s Optimal Profiles, these End of Life items will no longer be available in EasyApache. These items will be removed for the following reasons: They are no longer supported by their respective developers. They include known CVEs (Common Vulnerabilities and Exposures). EasyApache provides the most up-to-date, supported versions of Apache (2.2/2.4) and PHP (5.4/5.5). Keep in mind that viable alternatives to mod_frontpage exist, such as WebDAV and FTP. Also, PHP 5.2 and mod_frontpage will be available as custom modules (“opt mods”). To ensure that you receive up-to-date product news from cPanel, we encourage you to subscribe to the “Security Advisories and Product Release Announcements” mailing list here: http://cpanel.net/mailing-lists View the full article
-
A follow up on this recent network maintenance, we moved to a new primary internet provider, and the increase in performance has been outstanding! Everyone should have noticed a large improvement in response times overall connectivity performance. We are very happy to have top notch performance on our bandwidth and connectivity to the internet!
-
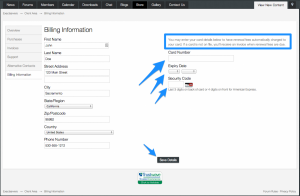
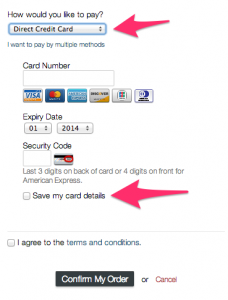
We have changed credit card processors recently, your credit card statements may show different information from in the past, the new information will be ExactServers / Sutter Solutions Inc. You can now also store your credit card info on your account, in doing so, each time an invoice is generated, if the card is valid, it will be auto billed and the payment applied to your account. This will help greatly for those if you who now pay manually each month/quarter/year etc. I would like to be clear that the credit card information is not stored locally, it is stored encrypted with merchant account processor, and in no way a security issue for you to be concerned with at all. All systems handling this information are PCI and PCI-DSS complaint. To store your credit card info, you can do this in the client area under "billing info" or when paying an existing invoice as well, simply select the option to store/save credit card info. Saving to your client area > billing information If you would like to save this information when paying an existing invoice, you can do so by selecting the "save my card details" If there are any questions please submit a ticket and we can assist you.
-
- Recurring Payments
- Billing
-
(and 1 more)
Tagged with:
-
1/28/2014 Houston, TX - cPanel, Inc. is thrilled to release cPanel & WHM software version 11.42, which is now available in the CURRENT tier. cPanel & WHM version 11.42 offers a brand new theme, an upgrade to Horde Groupware Webmail, and more. Paper Lantern Theme As part of 11.42, cPanel & WHM introduces Paper Lantern, a modern, powerful theme. With its simplified design, beautiful icon set, and thoughtful feature names, this edition of Paper Lantern is only the beginning. Horde Groupware Webmail Upgrade cPanel & WHM now uses Horde Groupware Webmail Edition 5.1. This upgrade provides a simple webmail application for all users, regardless of experience level. Detailed information on all cPanel & WHM version 11.42 features can be found at https://documentation.cpanel.net.* An overview of the latest features and benefits is also available at http://releases.cpanel.net. To ensure that you receive up-to-date product news from cPanel, we encourage you to subscribe to the “Security Advisories and Product Release Announcements” mailing list here: http://cpanel.net/mailing-lists. *Please note the updated URL for cPanel & WHM Documentation. View the full article
-
24 January 2014-12:16 PM We have scheduled a planned network maintenance for Friday Evening 10pm-12am PST https://t.co/WzA3flb3Ld
-
Enkompass version 3.0 will reach End of Life in February 2014. In accordance with our EOL policy [go.cpanel.net/eol], Enkompass will continue to function on servers after it reaches EOL. However, we will not provide further updates (for example, security fixes and installations) for Enkompass version 3.0 after it reaches its EOL date. Support for Enkompass will no longer be available in the ticket system, but community support is still available on our forums [http://forums.cpanel.net/enkompass-discussions.html]. So long, and thanks for all the fish. About cPanel, Inc. Since 1997, cPanel, Inc. has been a leading innovator and developer of control panel software for the web hosting industry. cPanel builds software that allows web host professionals to transform standalone servers into fully automated, point-and-click web hosting platforms. cPanel-licensed software allows server and website owners, along with resellers and developers, to optimize their technical resources and replace tedious shell-oriented tasks with dynamic, intuitive web-based interfaces. For more information, visit http://cpanel.net. For the PGP-signed message, see Enkompass-EOL. View the full article
-
We have scheduled a planned network maintenance window on Friday Jan 24 from 10PM-12AM PST. During this time, there may be short interruptions in service to Exact Servers Network. We will be upgrading some of our network hardware, and adding a new Internet provider, testing fail-over scenarios etc. We will do our best to keep any outages to a minimum. If you have any questions, let us know. Thank you Exact Servers / Sutter Solutions Inc
-
http://www.gametrailers.com/videos/rt3kca/the-final-bosman-demo-s-souls
-
We are releasing security patches for IP.Gallery 4.2.1 and IP.Gallery 5.0.5 to address a potential cross-site scripting issue related to the acceptance of SWF uploads. SWF (Shockwave Flash) is a file format used to embed flash movies in HTML documents, and when media files are accepted in IP.Gallery, SWF uploads are allowed. Because SWF files allow arbitrary script to execute within the context of the site they are hosted on, we are releasing a patch today which disables SWF files from being accepted by IP.Gallery by default. You may still allow SWF files after installing this patch by following the instructions in this knowledge base article, however we strongly recommend that you do not allow SWF submissions unless only trusted users are able to submit movies in your IP.Gallery installation. To apply the patch, please perform the following steps: Identify which version of IP.Gallery you are running. Download the appropriate patch file below Extract the contents locally on your computer Upload the contents of the "upload" folder to your forum root directory (where conf_global.php is located), overwriting any files when prompted. Please refer to this knowledgebase article if you are unfamiliar with using FTP to transfer files to your server. If you are an IPS Community in the Cloud customer running IP.Gallery 4.2.1 or above, no further action is necessary; we have already automatically patched your account. If you are using a version older than IP.Gallery 4.2.1, you should contact support to upgrade. If you are running IP.Gallery 4.2.1, please use the following zip: gallery_4.2-patch-Jan_3_2013.zip 5.01KB 9 downloads If you are running IP.Gallery 5.0.5, please use the following zip: gallery_5.0-patch-Jan_3_2013.zip 5.6KB 46 downloads As of the time of this post, the full IP.Gallery package in our client center has been updated. If you are running any version of IP.Gallery that is not listed above, we recommend that you upgrade to the latest version to obtain these security fixes, as well as several other security and bug fixes. We would like to thank Vasil A (Bulgaria) for bringing the vulnerability to our attention. View the full article